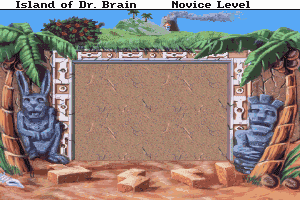
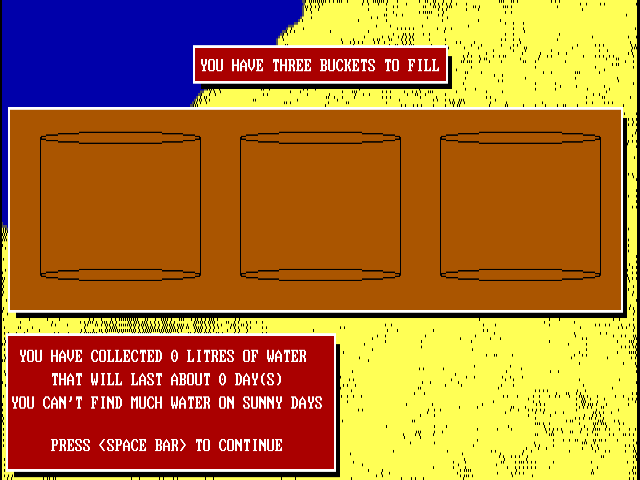
Island Conquest 2
DOS - 1996
Description of Island Conquest 2
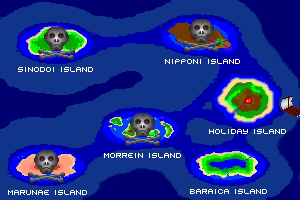
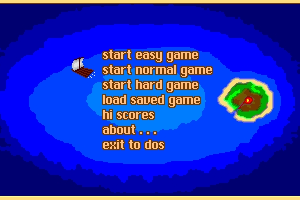
Here is the video game “Island Conquest 2”! Released in 1996 on DOS, it's still available and playable with some tinkering. It's a strategy game, set in a turn-based theme.
External links
Captures and Snapshots
Comments and reviews
LeChuck 2025-10-25 0 point
History of Software Piracy- Chronology and Consequences
Last Update: November 28, 2024
Welcome to our deep dive into the turbulent history of software piracy – a phenomenon as old as the software industry itself.
From the earliest days of home computing to the complex digital age of today, the history of software piracy is a fascinating journey through technology, law, and culture.
In the beginning, software was distributed freely among the small community of computer enthusiasts.
However, as computers became more mainstream and software more sophisticated, the industry saw the rise of proprietary models and the birth of application piracy.
This illicit practice quickly evolved, transcending simple disk copying to sophisticated online sharing methods.
Join us as we explore the milestones of this shadowy voyage. We’ll examine how piracy shaped the software industry, the ongoing battle between pirates and developers, and the ethical and legal dilemmas that continue to stir debate.
From bulletin board systems of the 1980s to the peer-to-peer networks of the 2000s, we’ll trace the evolution of piracy in step with technological advancements.
But it’s not just a story of conflict; it’s also a tale of how piracy influenced application accessibility and innovation, sometimes pushing the industry towards more user-friendly models and pricing strategies.
Embark with us on this intriguing exploration of the history of application piracy – a saga of rebels, innovators, and the relentless pursuit of digital freedom.
Blog Middle Component Image
Protect Your Brand & Recover Revenue With Bytescare's Brand Protection software
Book a Demo
What is Software Piracy?
Software piracy is the unauthorised copying, distribution, or use of application.
It involves the infringement of copyright laws designed to protect the intellectual property rights of software creators. Here are the key aspects of application piracy:
Unauthorised Copying: This is the most common form of application piracy. It occurs when someone copies a software program without the permission of the copyright holder. This can happen in various ways, such as installing a program on more than one computer contrary to the terms of the software’s license agreement, or copying a friend’s software.
Counterfeiting: Counterfeit software is an illegal reproduction of genuine application. It’s often sold as though it were legitimate, often with fake packaging and documentation that mimic the original product.
Internet Piracy: This involves the distribution of pirated application over the Internet. This can occur through peer-to-peer networks, illegal download websites, or file sharing.
Corporate Piracy: Also known as commercial piracy, this happens when businesses use unlicensed copies of application. This can range from a single unlicensed copy used within a business to a company-wide practice of installing multiple unauthorised copies for employee use.
End-User License Agreement (EULA) Violations: This form of piracy occurs when users violate the terms of the application’s EULA, such as by using the application in ways not permitted by the agreement or ignoring restrictions on copying and distribution.
Further Reading: How to Report Software Piracy
Consequences of Software Piracy
The consequences of application piracy are far-reaching and can affect various stakeholders, from the software creators to the end users. Here’s an overview of the major consequences:
Legal Repercussions: Software piracy is illegal and can lead to severe legal consequences for both individuals and organisations. These can include fines, legal fees, and in some cases, criminal charges.
Economic Impact on Developers: Software developers and companies suffer significant financial losses due to piracy. This lost revenue can impact their ability to invest in research and development, ultimately hindering innovation and the quality of future application products.
Security Risks: Pirated application often lacks critical updates and security patches, making it more vulnerable to malware, viruses, and other security threats. Users of pirated application risk compromising their systems, which can lead to data theft, loss, or damage.
Reduced Support and Updates: Legitimate application users receive customer support and regular updates, including security patches. Pirated application typically does not have access to these benefits, leading to performance and security issues over time.
Harm to Reputation and Ethics: Businesses and individuals caught using pirated application can suffer reputational damage. For businesses, this can impact customer trust and corporate relationships. It also raises ethical concerns about respecting intellectual property rights.
Impact on Economy: The widespread use of pirated application can negatively impact the economy. It affects not only the application industry but also reduces tax revenues and can harm job creation in the tech sector.
Quality Compromise: Pirated application may be altered or stripped of key features, resulting in a subpar user experience compared to the legitimate version. Users may not get the full functionality or performance they expect.
Increased Costs in the Long Term: For businesses, the initial savings from using pirated application can be offset by the costs associated with legal actions, system failures, security breaches, and loss of data.
Negative Impact on Innovation: The financial losses due to piracy can limit the resources available for developers to innovate and improve their products, slowing down technological advancement in the application industry.
Must Read How to Protect Video from Piracy
Further Reading: 7 Reasons Why Piracy is Bad
Blog Middle Component Image
Protect Your Brand & Recover Revenue With Bytescare's Brand Protection software
Book a Demo
History of Software Piracy
The history of application piracy is closely intertwined with the evolution of computing and the industry. Here’s an overview:
Early Days of Computing (Late 1970s – Early 1980s):
In the early years of personal computing, software was often shared freely among users. The concept of software as a commercial product was still emerging, and many in the computing community saw application sharing as a normal practice.
The rise of home computers like the Apple II and Commodore 64 made application more accessible, leading to the first instances of widespread application piracy. Users would copy floppy disks and share them with friends or through mail-order services.
The Growth of the Software Market (Mid-1980s – Late 1990s):
As the application market grew, companies began to see the financial impact of piracy. They started to implement copy protection and anti-piracy measures. This led to a sort of arms race between software companies and pirates.
Bulletin Board Systems (BBS) became popular in the 1980s for sharing cracked application, known as “warez”. These were early forms of online communities where users could download pirated application.
The Internet Era (Late 1990s – 2000s):
The advent of the internet changed the landscape of application piracy. File-sharing platforms like Napster, which was initially used for music, also facilitated the sharing of application.
The rise of peer-to-peer (P2P) networks in the early 2000s, such as BitTorrent, further escalated software piracy. It became easier and faster to distribute large application files globally.
Modern Developments (2010s – Present):
Software companies began shifting towards subscription-based and cloud-based models, like Adobe’s Creative Cloud and Microsoft Office 365. This made traditional forms of piracy less effective.
Despite these changes, application piracy still exists. Modern pirates often use sophisticated methods to bypass application activation and licensing checks.
The rise of mobile computing and app stores introduced new forms of piracy, particularly with the unauthorised distribution of paid mobile apps.
Must Read Laws Against Software Piracy in India
Legal and Ethical Shifts:
Throughout its history, application piracy has been met with legal challenges. Software companies have taken pirates to court, and there have been several high-profile lawsuits.
Governments around the world have enacted stricter copyright laws and international agreements to combat application piracy.
There’s also a growing ethical awareness about the impacts of piracy on the application industry, leading to more emphasis on legal application use, especially in educational and corporate environments.
How to Prevent Software Piracy?
Preventing application piracy requires a multifaceted approach involving technological solutions, legal measures, and public awareness. Here are some effective strategies:
Write a comment
Share your gamer memories, help others to run the game or comment anything you'd like. If you have trouble to run Island Conquest 2, read the abandonware guide first!
Download Island Conquest 2
We may have multiple downloads for few games when different versions are available. Also, we try to upload manuals and extra documentation when possible. If you have additional files to contribute or have the game in another language, please contact us!
DOS Version
Similar games
Fellow retro gamers also downloaded these games:

 286 KB
286 KB